
In today’s digital world, the threat of cyberattacks keeps everyone on their toes. The projected losses from data breaches, expected to soar past $5 trillion by 2024, are no small concern.
Cybercriminals are getting craftier, putting big names like Marriott International and Yahoo and the little guys in the firing line—small businesses take a hit in 43% of cyberattacks, according to Accenture.
This scenario makes picking a web hosting provider as solid as a rock crucial. I mean, it’s your digital fort, right?
But if you pick Cloudways, you won’t have to worry about server security as our servers come pre-equipped with features like Firewalls and Port Security, Database Security, Application Isolation, and much more.
In this blog, we’ll tell you what features Cloudways offers for comprehensive server security. And just to cover all bases, we’re throwing in a server security checklist in case you are exploring options other than Cloudways.
Let’s get started…
What Is Server Security?
Server protection security in web hosting is a set of precautions to safeguard against diverse threats.
It’s about protecting the server from attacks that try to overload it (DDoS attacks), stopping people from guessing passwords too many times (brute force attacks), and ensuring users don’t mess things up on purpose or by mistake.
The protective measures involve maintaining firewalls, ensuring strong password policies and user authentication protocols, deploying antivirus software, and routinely backing up data to avert potential losses.
Essentially, it’s about fortifying the security of a web hosting server to ensure smooth and secure operations. When selecting a hosting provider, be sure to refer to our guide on 10 key factors to consider in web hosting security.
Why Is Server Security Important?
When you’re considering web hosting, it’s all about making sure the digital space where your business data lives is rock-solid. Here’s why having a well-protected server matters:
1. Reliable Information: Good web server security ensures that your stored data is accurate and complete, like a safeguard against unwanted changes.
2. Always Accessible: Security measures keep your digital space open for business, ensuring it’s available whenever you or your authorized users need it.
3. Securing Sensitive Data: Your server acts as a secure vault. Strong security prevents unauthorized access to sensitive information, keeping it confidential.
4. Protecting Your Business Image: A security breach could harm your business reputation and lead to financial losses. A secure server acts as a protective shield against such incidents.
5. Compliance with Rules: Big companies have specific rules to follow. Web hosting with solid security ensures your digital space meets these rules, avoiding fines and maintaining legitimacy.
So, when you’re in the market for web hosting, think of it as finding a reliable digital space with strong security measures in place.
Web Hosting Server Security Issues
If you’re exploring web hosting, you might wonder about typical security issues. Here are key considerations for those seeking a hosting service with robust server security:
1. Vulnerabilities to Attacks: Look for hosting services addressing vulnerabilities that could make your site a target. The right provider should actively shield against common cyber threats.
2. Weak Authentication Practices: Ensure the hosting service has strong user authentication measures. This is like having a secure lock on the virtual door to your website.
3. Insufficient Backup Procedures: Check if the hosting service regularly backs up data. It’s like having a safety net—important in case anything unexpected happens.
4. Outdated Software Risks: Opt for a service that updates server software. This is similar to regularly installing updates on your computer for better performance and security.
5. Lack of DDoS Protection: Confirm the hosting service has defenses against Distributed Denial of Service (DDoS) attacks. It’s akin to having guards to prevent overcrowding and disruptions.
We don’t want to brag, but — if you don’t want to break a sweat worrying about these common security concerns, consider Cloudways, a web hosting provider with robust server security features already built-in.
Strengthen Your Website Security With Cloudways Server Protection
Benefit from a dedicated firewall, automated protection with Fail2ban, security patches, bot protection, vulnerability scanning, and free 1-Click SSL.
Cloudways’ Server Security Features
Now, we’ll explore the intricate security features that make Cloudways a powerhouse in ensuring the security of your server.
1. DDoS Mitigation
DDoS attacks stand as potential disruptors to your server’s stability. To counter this, Cloudways incorporates Layer 3 & 4 DDoS Mitigation. This acts as a protective shield, fortifying your server’s resilience.
Collaborating with leading cloud providers, Cloudways ensures your server remains steadfast even when faced with intense DDoS attacks. It’s a precautionary measure, safeguarding your online presence and preserving accessibility.
If you’re thinking of hosting a WordPress site on Cloudways, you might find this guide on how to stop WordPress DDoS attacks helpful.
2. Vulnerability Scanner
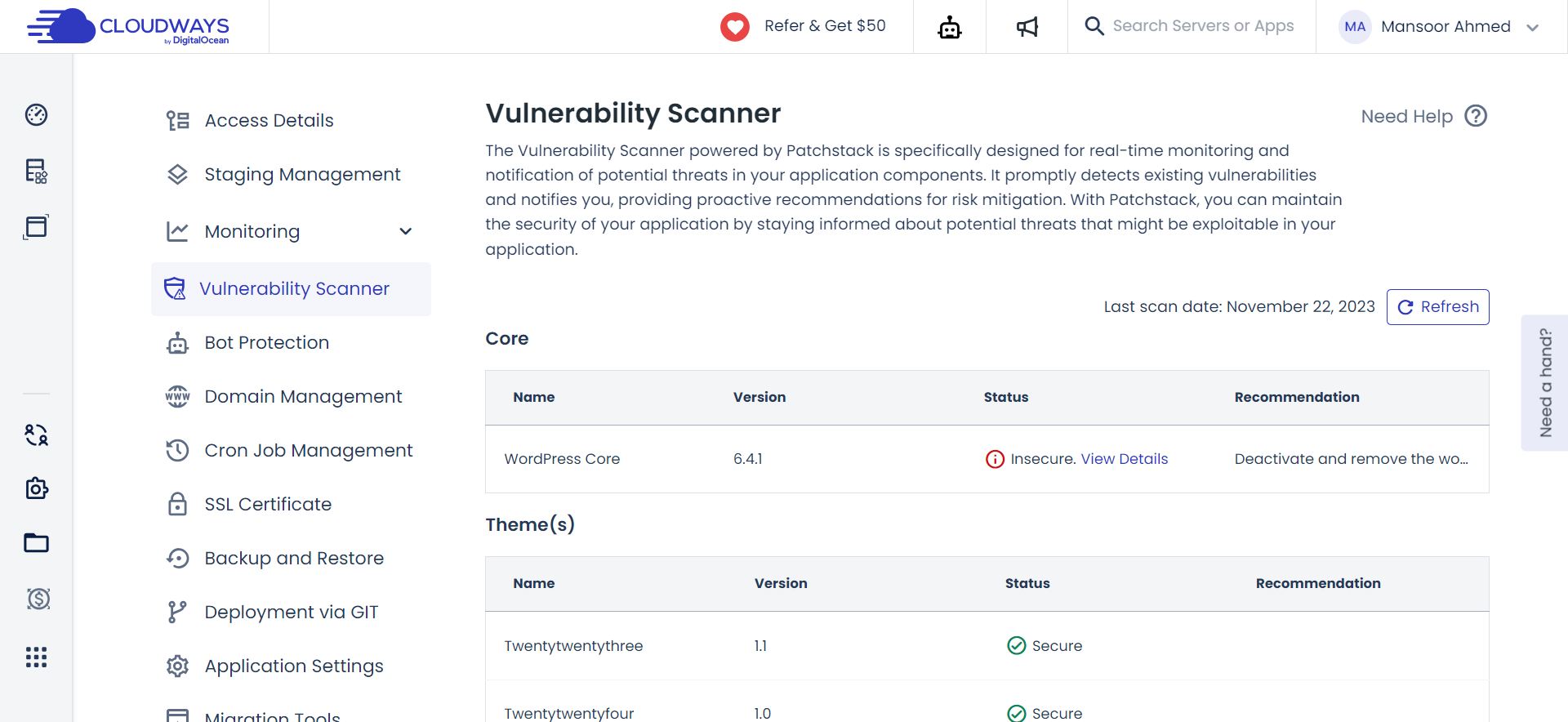
Navigating the dynamic landscape of online threats can be challenging, especially when it comes to identifying vulnerabilities in your WordPress core, plugins, and themes. Cloudways introduces the Vulnerability Scanner, powered by Patchstack.
This feature serves as a vigilant watchman, providing instant notifications and conducting continuous audits. It’s an ally in maintaining a secure environment, alerting you to potential risks, and enabling timely action.
3. Free SSL Certificates
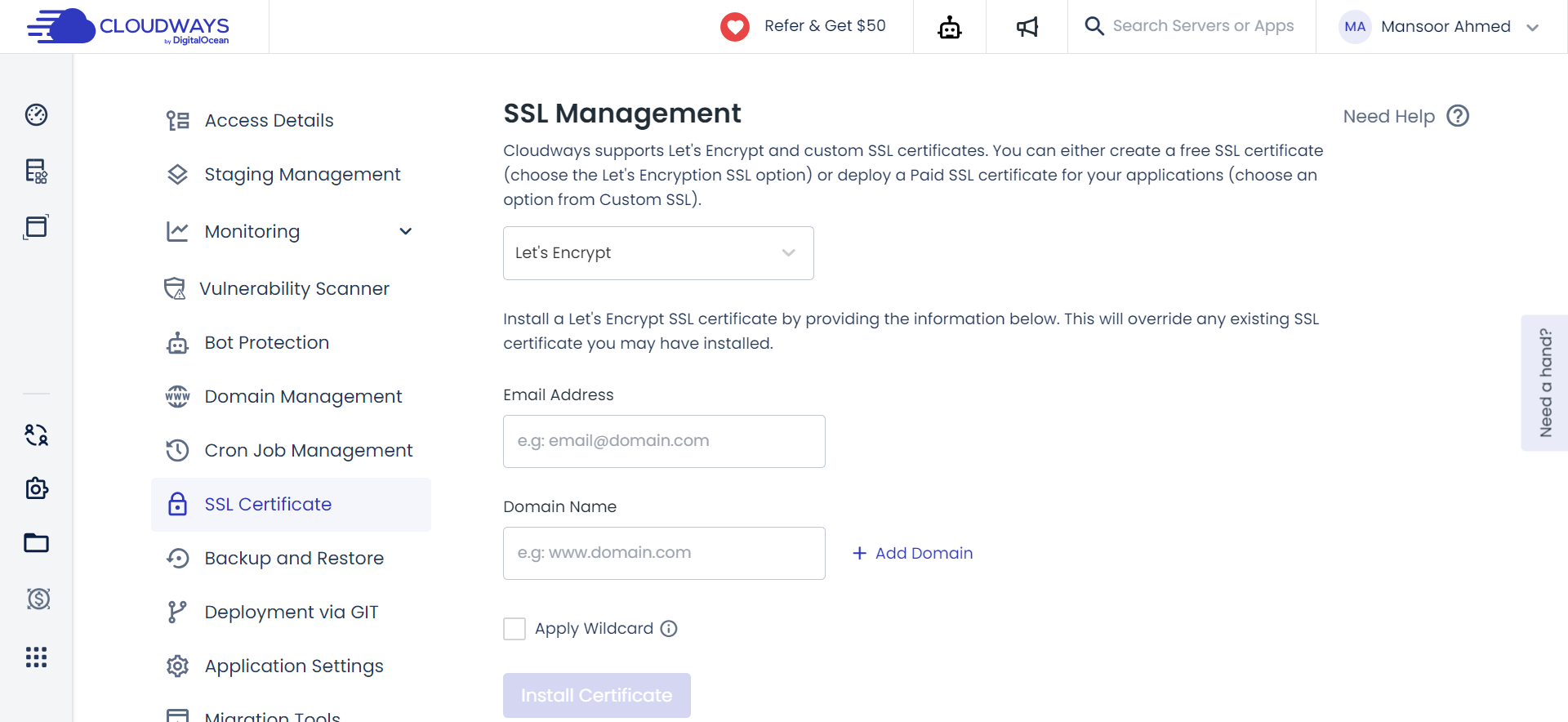
In an era where online trust is paramount, securing your website with SSL is crucial. Recognizing the complexity and cost associated with this process, Cloudways simplifies it with 1-Click Free SSL.
This built-in Let’s Encrypt SSL not only secures your data in transit but also fulfills HTTPS requirements. It’s a straightforward solution, enhancing the security of your website without additional complexities.
4. IP Whitelisting
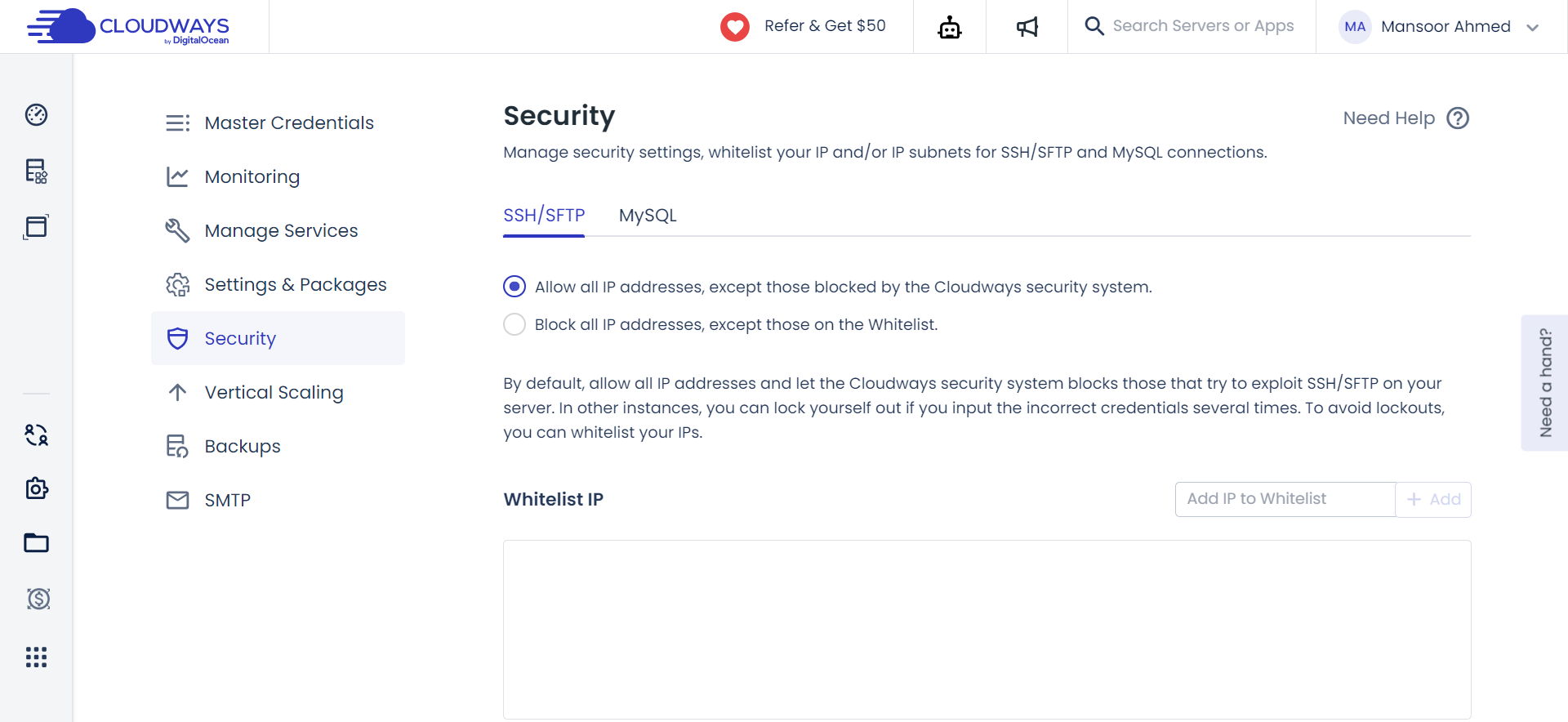
Collaborating on a server often involves the challenge of providing secure access to specific networks or regions.
Cloudways addresses this challenge with IP Whitelisting. This feature streamlines collaboration by allowing you to whitelist specific IPs, ensuring unrestricted access to SSH and SFTP. It’s a practical approach, enhancing security while facilitating seamless collaboration.
5. Regular Security Patches
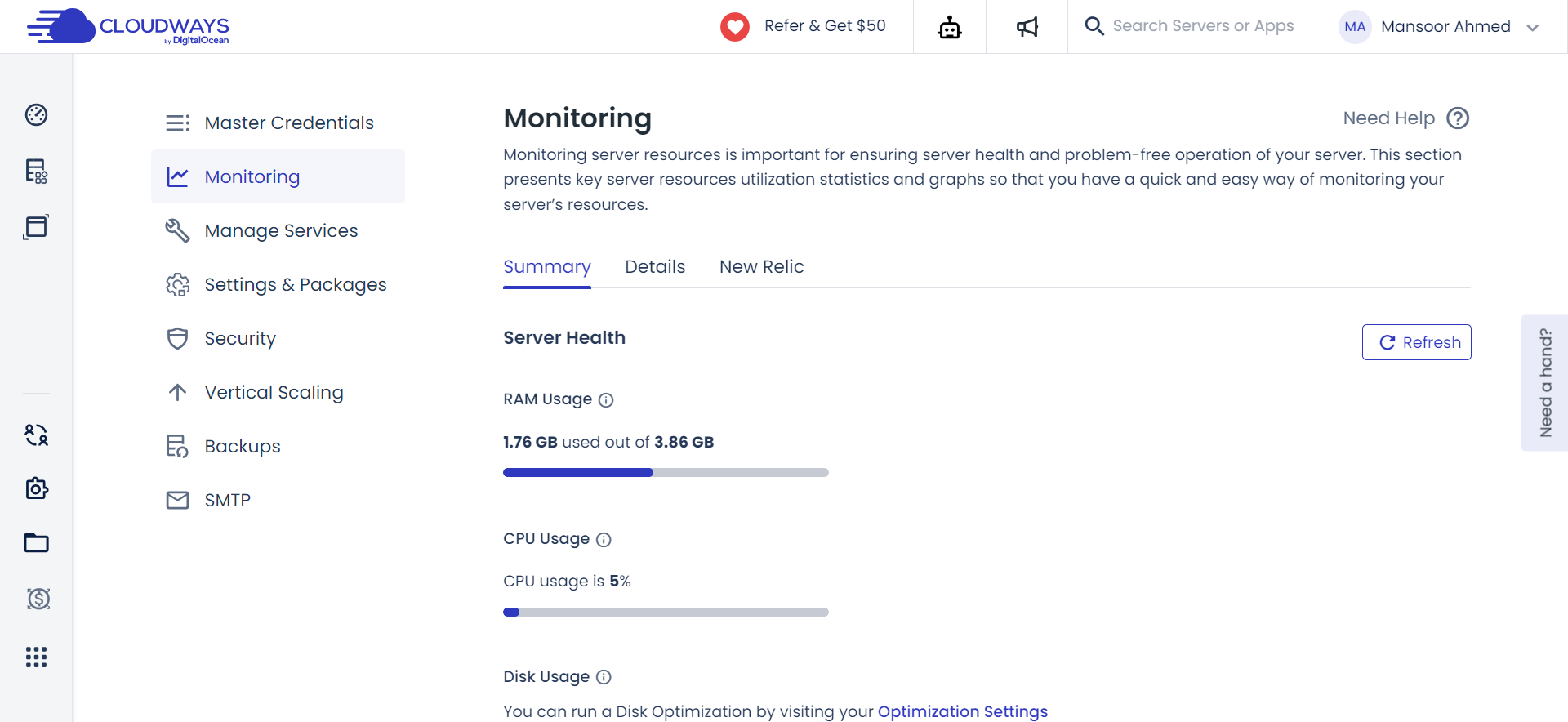
Maintaining server software up-to-date is essential for security. However, managing regular OS patches manually can be time-consuming.
Cloudways alleviates this burden with regular security patches. It’s a proactive approach, ensuring your server stays secure and up-to-date. This ongoing effort minimizes vulnerabilities, contributing to a robust and well-maintained managed cloud server.
6. Automated Protection with Fail2Ban
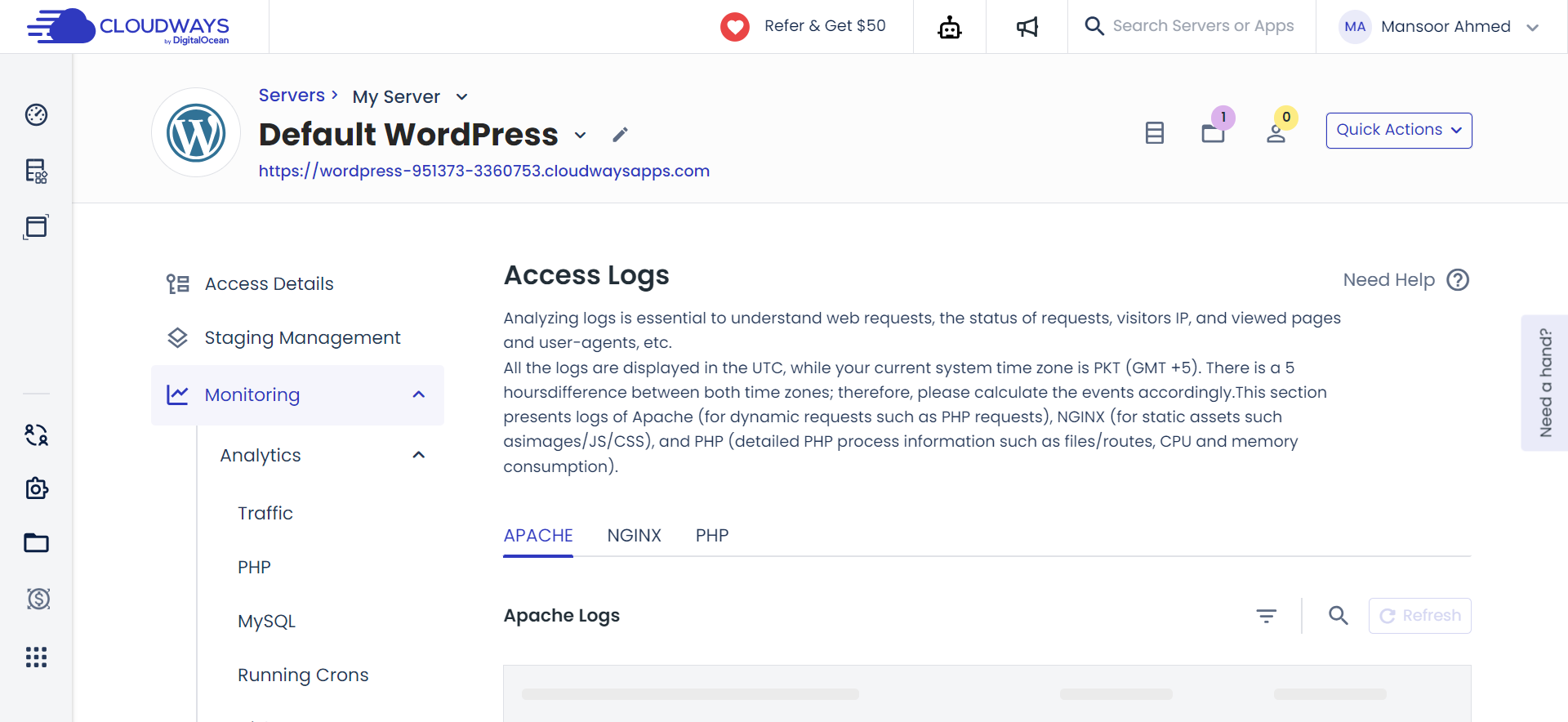
The threat of brute force attacks is ever-present, and manually monitoring logs to thwart them can be impractical.
Cloudways introduces automated protection with Fail2Ban. It acts as a digital security guard, intelligently monitoring logs and blocking IPs attempting password breaches or exploiting vulnerabilities. This automated protection ensures a safer server environment without constant manual intervention.
7. Dedicated Server-Level Firewalls
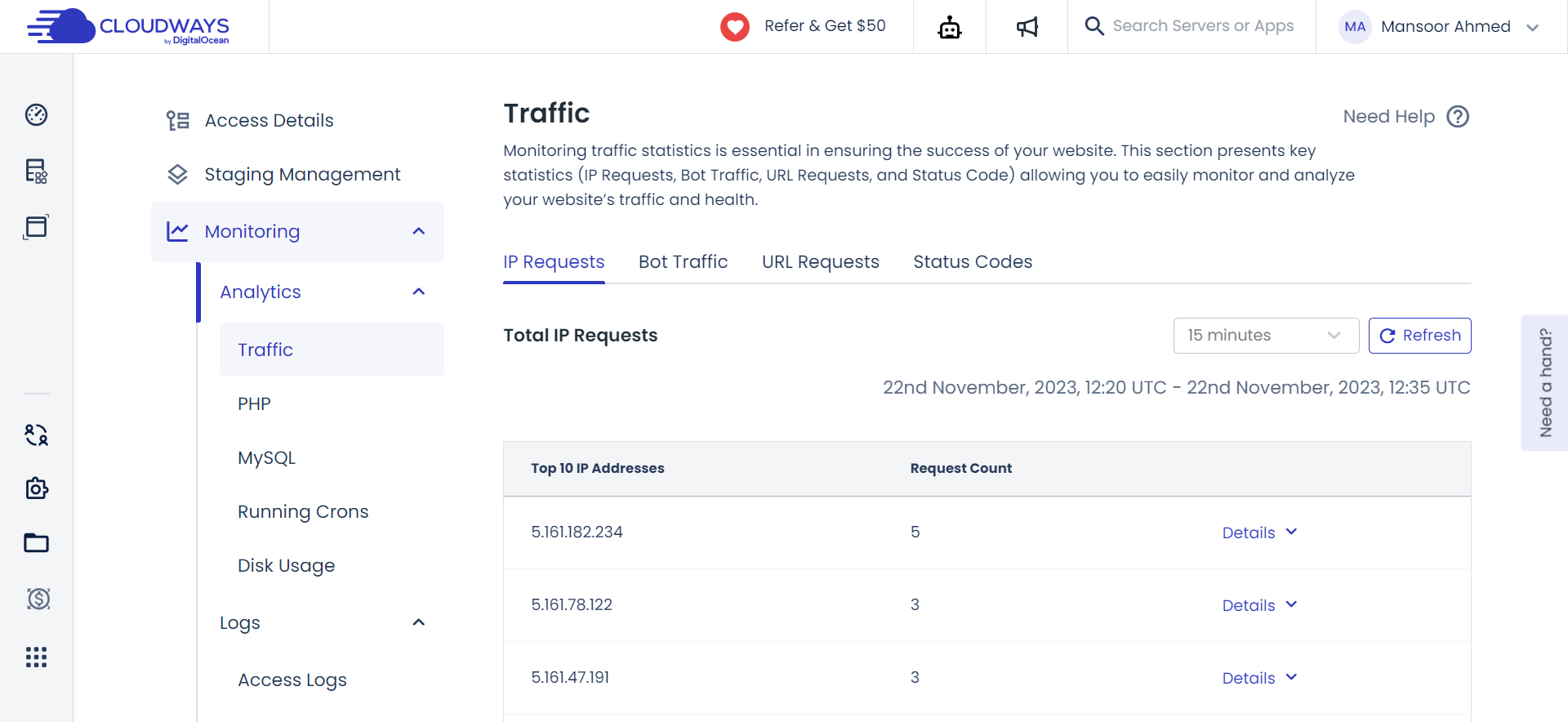
Malicious traffic poses a constant threat to server security.
Cloudways implements dedicated server-level firewalls powered by Shorewall. These serve as vigilant guards, filtering out malicious traffic and establishing a reliable barrier against potential intruders. It’s a security measure akin to having a trusted gatekeeper for your server.
8. Bot Protection
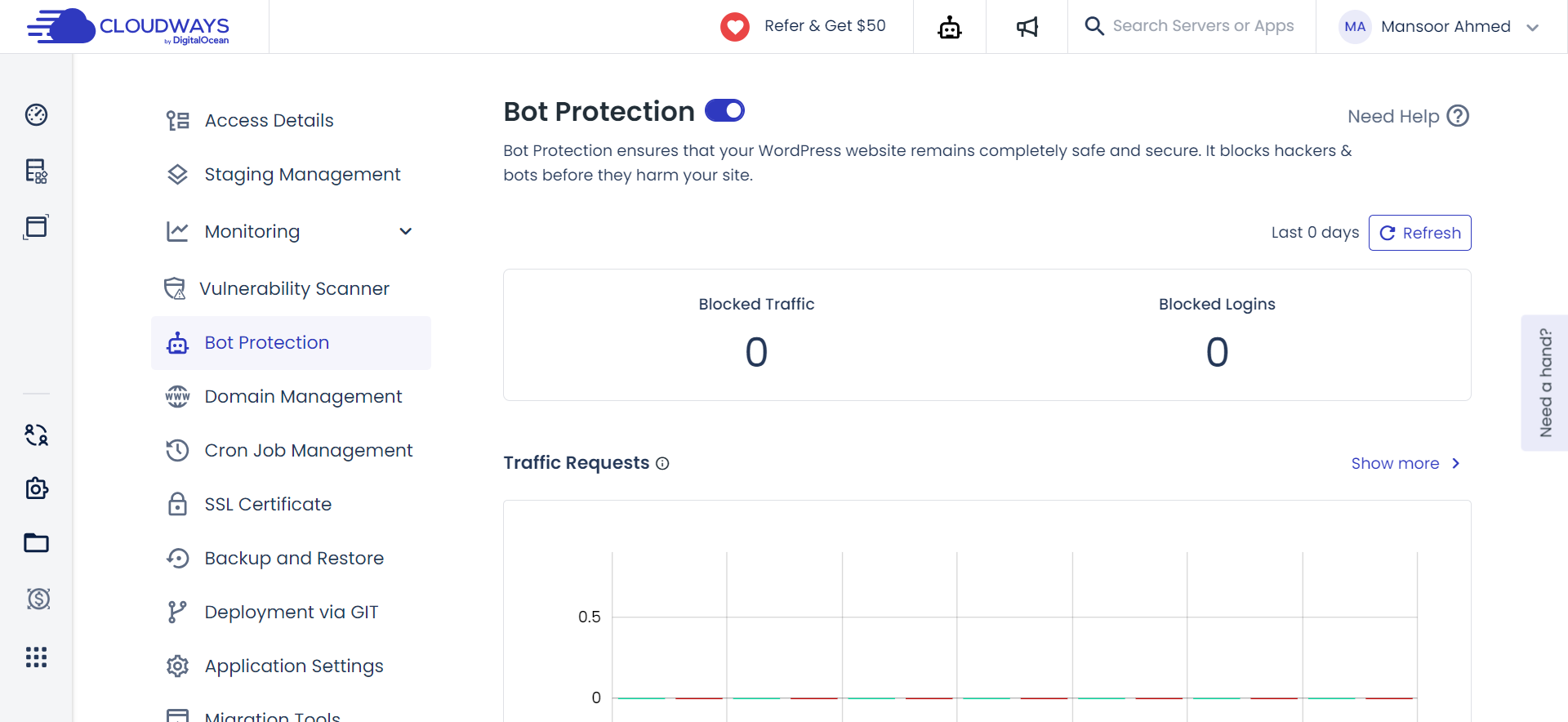
Defending against bots, login attacks, and DDoS threats is a collective effort at Cloudways, thanks to their partnership with MalCare.
This collaboration ensures uninterrupted services, protecting servers from disruptive digital forces. It’s a strategic alliance, ensuring the continuous availability of your services.
Learn more about the Cloudways Bot Protection feature here.
9. SafeUpdates
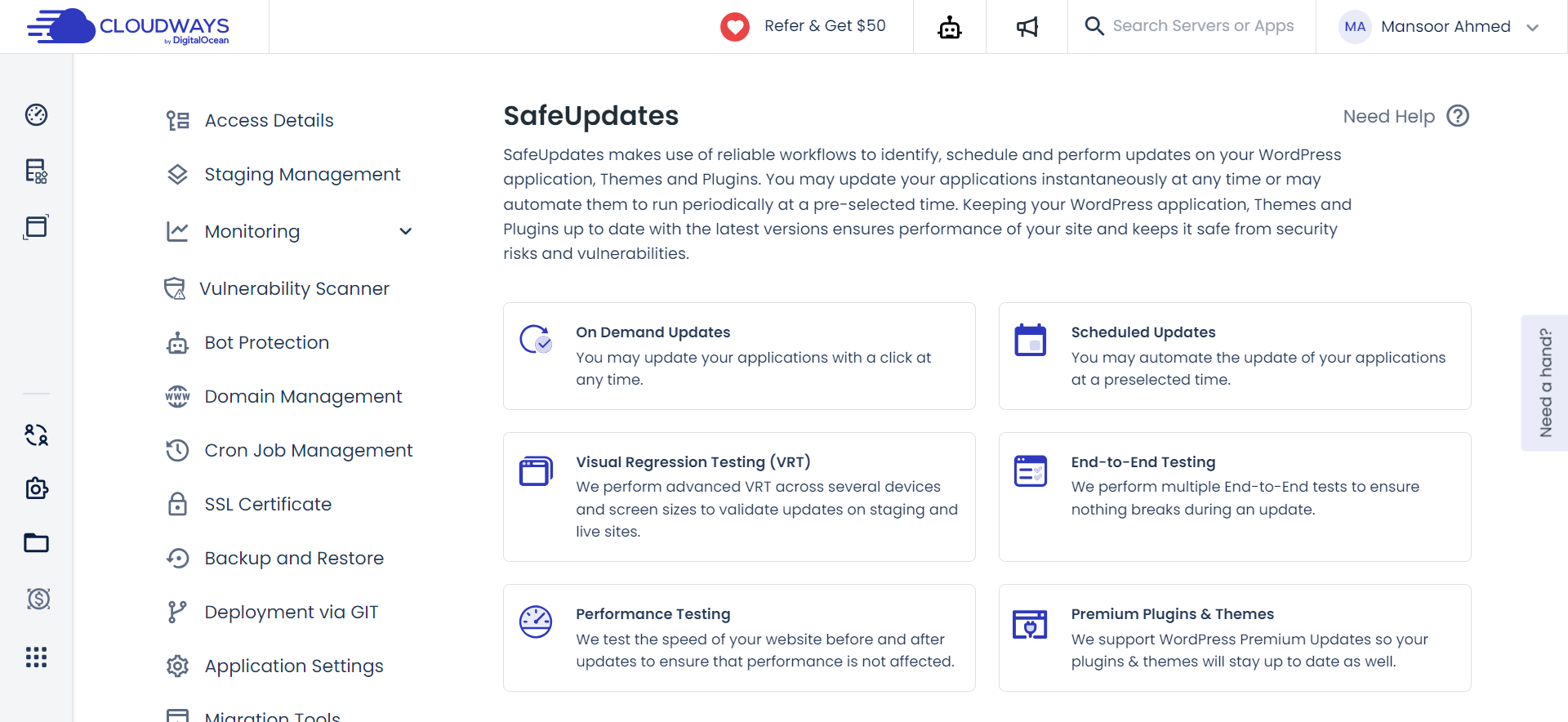
Managing WordPress updates, though crucial, can be cumbersome. Recognizing this, Cloudways introduces SafeUpdates.
This automated assistant streamlines the process, handling the detection, staging testing, and deployment of WordPress core, theme, and plugin updates. It’s a time-saving solution, allowing users to focus on business growth without worrying about potential hiccups in the update process.
All these features position Cloudways as the top choice for individuals seeking a web hosting provider with robust server security features, making it the ideal platform for hosting mission-critical sites.
Server Security Checklist
When selecting a web hosting provider for your critical websites, it’s essential to assess the server’s security features. Here’s a checklist of server security features, along with explanations, allowing you to compare Cloudways with other providers and make an informed decision:
1. DDoS Protection
Ensure your hosting provider offers protection against Distributed Denial of Service (DDoS) attacks. This safeguard prevents overwhelming your server with traffic and maintains accessibility during cyber threats.
2. Regular Security Audits
Look for hosting providers that conduct regular security audits. This practice involves reviewing and assessing server configurations and logs to identify and address potential vulnerabilities.
3. SSL Certificate Support
Check for SSL certificate support, a fundamental security measure for encrypting data in transit. Hosting providers should offer options for easy implementation, such as Let’s Encrypt SSL.
4. IP Whitelisting and Access Control
Verify if the hosting service allows you to whitelist specific IPs, providing controlled access to your server. This feature enhances security by limiting access to authorized networks or regions.
5. Operating System (OS) Updates
Ensure the hosting provider regularly updates the server’s operating system. Prompt OS updates are vital for patching vulnerabilities and maintaining a secure server environment.
6. Brute Force Protection
Look for mechanisms like Fail2Ban or similar solutions that protect against brute force attacks. These tools monitor logs and automatically block IP addresses attempting unauthorized access.
7. Firewall Protection
Check if the hosting provider employs server-level firewalls to filter malicious traffic. Firewalls act as barriers, preventing unauthorized access and enhancing overall server security.
8. Bot and Malware Protection
Assess whether the hosting service includes features to defend against bots and malware. Collaborations with external services, like Malcare, can add an extra layer of protection against disruptive digital threats.
9. Automated Update Processes
Evaluate if the hosting provider offers automated update processes for server components, including the operating system, web server software, and other critical applications. Regular updates are crucial for patching security vulnerabilities.
Summary
In the dynamic realm of online security, choosing a web hosting provider that prioritizes robust server security is essential. Cloudways, for instance, is committed to implementing and maintaining strong security measures.
Tailored for users without advanced technical skills, Cloudways ensures a secure hosting environment, defending against potential cyber threats. Selecting such a provider is a proactive step towards safeguarding your online presence in a world where cybersecurity challenges persist.
Q1. What are the main types of server security?
A. The three main types of server security are physical, network, and host. Network connections are safeguarded by firewalls, preventing unauthorized access.
Q2. How can I secure a server effectively?
A. Update and upgrade software regularly, remove unnecessary services, hide server information, use intrusion detection systems, perform file and service auditing, and set up a firewall. Regular backups are crucial.
Q3. What is the risk associated with servers?
A. Server risk involves outdated software, as aging software can have vulnerabilities exploited by cybercriminals. Regular patching is essential to prevent the exploitation of known weaknesses and to enhance security.
Abdul Rehman
Abdul is a tech-savvy, coffee-fueled, and creatively driven marketer who loves keeping up with the latest software updates and tech gadgets. He’s also a skilled technical writer who can explain complex concepts simply for a broad audience. Abdul enjoys sharing his knowledge of the Cloud industry through user manuals, documentation, and blog posts.