Cyber attack analysis by Cloudways reveals the year’s last three months (Oct to Dec) as the most vulnerable period for shoppers and online businesses.
The threat of a cyber-attack poses a danger to businesses, employees, and their customers. And a successful security breach can annihilate an organization’s reputation and impose severe financial distress.
Therefore, cyber security is a priority for all online businesses. And if that’s not the case for your business? Our latest data study reveals why a lax approach to securing sensitive data isn’t a risk worth taking.
TechRepublic’s research suggests that 45% of customers would not interact with a business after it has experienced a successful cyber attack. Small businesses are especially mindful, with research suggesting that 60% of SMBs fall victim to cyber-attacks within the first six months of operation.
We’ve reviewed ITGovernance data on security breach frequency to determine the most dangerous months for online businesses and consumers. And we’ve presented this data in a simplified form, with actionable advice to help ensure your business retains customer trust and is prepared to handle the looming threat of cyber attacks.
Which Is the Most Dangerous Month for Cyber Attacks?
Businesses are warned: Our data has revealed the months falling in the holiday season as the most dangerous period for cyber attacks. Black Friday, Cyber Monday, and the holiday sales occur during this season (Oct to Dec), posing a risk to businesses looking to capitalize on the peak sales period.
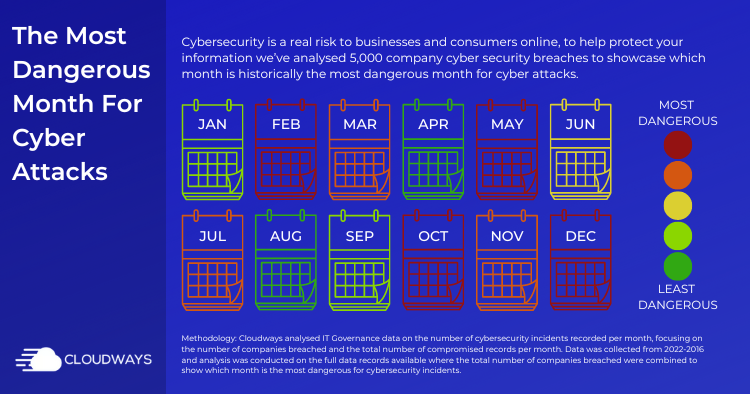
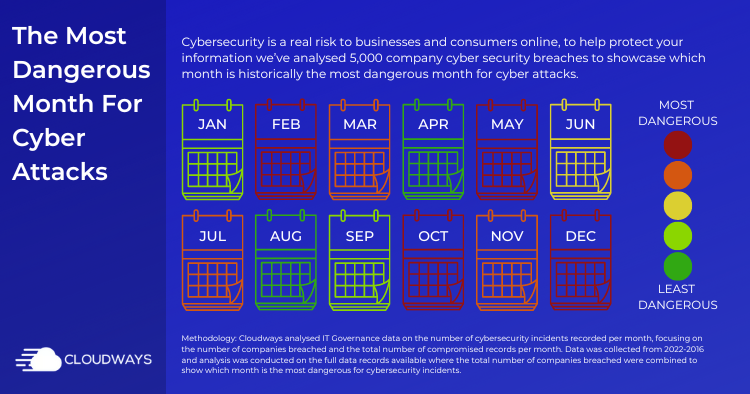 The calendar showcases the most & least dangerous months for online businesses for cybersecurity breaches.
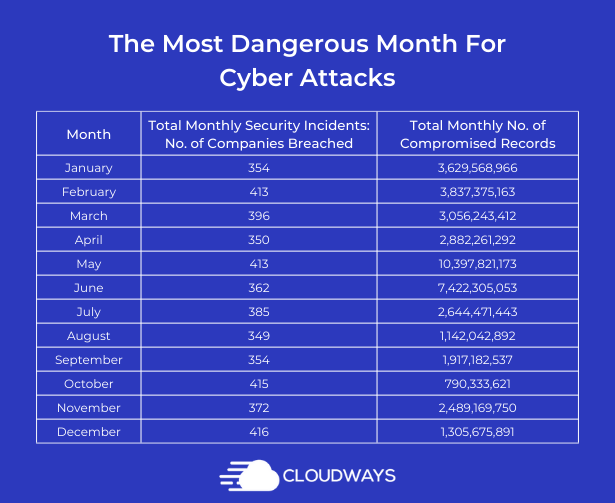
The calendar showcases the most & least dangerous months for online businesses for cybersecurity breaches.We identified December as the highest cyber security risk to businesses. An average of 83 companies fall victim to a data breach in December every year, leading to an average of 261,135,178 breached records – that’s, people’s confidential data being compromised, stolen, and viewed by cybercriminals.
Also, the months of February and March (shortly after the holidays) have also been revealed as vulnerable to frequent cyber attacks.
In 2022, this period infamously became synonymous with Lapsus$, a digital extortion group that emerged in December to steal source code and other valuable data from Nvidia, Samsung, and Ubisoft. The attacks continued into March when the group claimed to breach Microsoft Bing and Cortana, also compromising the source code.
“A multi-layered defense strategy is the best way forward… when it comes to security, you should leave nothing to chance.”
– Paul Haverstock, Cloudways
Overall, cybersecurity breaches have compromised more than 4,579 businesses since 2017.
Are the holidays canceled because of cyber threats? Of course not. We can defend our businesses against cyberattacks via preparation and education.
Quoting Paul Haverstock, VP of Cloudways Engineering, “a multi-layered defense strategy, whereby multiple defenses are layered on top of one another, is the best way forwards. When it comes to security, you should leave nothing to chance“.
This is why our optimized cloud-based web hosting solution comes with multi-faceted features like SSL, TFA, and end-to-end encryption to protect your business. Our layered defense strategy allows your business to efficiently manage its online presence while bolstering its cyber security defenses.
How to Protect Your Business From Cyber Attacks
A good reputation is built on trust. And if your business fails to secure your client’s information, it’d become impossible to regain their confidence.
Common cyber attack threats include financial fraud, phishing scams, Trojan horses, and DDoS attacks. Some threats are highly sophisticated and need a secure firewall, while others are quite dull and use brute force.
An example of a weak attack is a lousy attempt at guessing passwords that could provide access to your website if the right processes aren’t followed correctly.
You can secure your business’ online presence by following these six essential steps:
1. Invest in Secure Systems
You cannot ensure 100% protection from flawless phishing attacks sent from within internal software. The more critical data you have, the more shielding it will need from sophisticated cyber attacks.
Arranging secure hosting with high-end security, such as Cloudways with its Cloudflare CDN integration, prevents your back-end systems from developing weak points. It also protects against computer viruses, Trojan horses, and spyware that can steal, encrypt, delete, alter, or hijack user information.
2. Safeguard Key Login Details
The more widely you share important login information, the more vulnerable it becomes. If someone requests a file or specific information, have a trusted user source it instead.
If a new user requests broad access, the best practice is to provide obscured login details through a password manager that you control centrally. Examples include LastPass, NordPass, and Dashlane.
3. Shield Customer Data
Keeping track of your customer data is vital, and businesses should clearly understand the type and usage of their data. Understand that people’s personal information is precious, and compromising it will result in losing all trust in your market.
We advise you to store customer data in an encrypted system and provide access to only authorized accounts through a secure gateway.
4. Establish Emergency Procedures With Employees
When employees believe they’ve received urgent demands from their employers, they feel pressured to act immediately. Cyber attackers will leverage this trust to steal information and access sensitive data.
Corporations must be clear on why and when they might reach out to workers with emergency requests, explaining how they can verify legitimacy. Vitally, employers also need to stress which requests they’ll never make, like demanding immediate bank transfers without using standard payment processes.
5. Check Emails for Red Flags
Ransomware attack attempts often come through email – which makes analyzing email domains, content, and sender information vital before acting on requests.
Email domains are tough to flawlessly spoof (almost impossible). A close examination could reveal extra or substituted characters if an email seems to be sent from the right domain. Often, a phishing email has a domain that doesn’t fit the content at all.
6. Keep All Systems Updated
Updating key operating systems and security software is vital for cyber security. Attackers target outdated software to obtain valuable data from neglected websites.
Ensuring all operations are updated for websites or business owners can be very time-consuming. However, the automatic SafeUpdates technology systematically runs secure updates in the background, saving you time, energy, and costs.
7 Ways Consumers May Protect Their Data Online
As a consumer, you can also take practical steps to secure your sensitive information. Making simple changes to managing your online presence can prevent unwanted attempts to access your data.
Here are seven best practices to help consumers avoid cyber attack threats:
1. Only Use Secure Websites
Look for a padlock icon when you land on a website for the first time. Does the address start with https rather than http? If so, you’re safe to continue browsing; if not, exit the site and find a secure alternative.
2. Beware of Suspicious Emails
Like businesses, consumers primarily receive phishing scams through email. When running on autopilot, ‘phishing’ emails may catch you off-guard. So, be aware of the key giveaways of a suspicious email, like text littered with mistakes and inconsistencies, an overbearing sense of urgency, and a phony-looking email domain.
3. Use Strong Passwords
Research suggests that a quarter of Americans have used an easy-to-guess password like “123456” or “password” and use the same password across multiple online accounts. Weak or repeated passwords present a severe security risk, so ensure you use unique passwords that combine length and complexity.
4. Update Software and Devices Regularly
Attackers regularly target outdated software versions since they often contain known vulnerabilities. So, you must update your software and devices as soon as new releases become available to safeguard yourself from intrusions.
5. Avoid Purchasing Over Public Wi-Fi
When you access publicly-available Wi-Fi (in a coffee shop or an airport, for example), you often use an unsecured public network, meaning your data is at greater risk of being stolen.
6. Be Careful on Social Media
Never accept a friend or follow request from users you don’t know, so take time to ensure you trust the account before clicking the ‘accept’ button. You should also review your privacy settings across your social media accounts, enabling you to control who can and can’t see what you post.
7. Never Give Out Personal Information
Never knowingly give out personal information unless you’re absolutely sure the request is legitimate and from a trusted contact or organization. Most legitimate companies will never ask you to provide personal information, particularly over email or SMS. If they do, verify the request first by visiting their website and contacting them directly.
Campaign Methodology – Finding the Most Dangerous Month
Cloudways analyzed IT Governance data on the number of cybersecurity incidents recorded per month, focusing specifically on the number of companies that breached and compromised records per month.
The data is based on the dates of breaches reported, not when they occurred. And this data was collected from 2022-2016. We analyzed the full data records available, giving a range of February 2022-March 2017 to provide a comprehensive five-year analysis.
The five-year data span calculated the total number of companies that breached and compromised monthly records. The result shows which month is the riskiest for cybersecurity incidents. Data was collected & analyzed in July 2022.
Start Growing with Cloudways Today.
Our Clients Love us because we never compromise on these
Cloudways
Cloudways is a European MSP that provides custom cloud design, deployment and management solutions on leading cloud providers.